
What is Biometric Spoofing?
Biometric technology is proven to be a more secure alternative to other access control systems, such as key cards or pins and passcodes. This is because biometric systems use an individual person’s unique genetic makeup as the access ‘key’, making it far more difficult to replicate.
However, replications aren’t always impossible in biometric technology and some less sophisticated biometric systems can be fooled by fake representations of a piece of biometric data. That’s why ievo implement liveness detection as a feature that can be activated across the entire range of the Ultimate fingerprint scanners.
ievo readers have the unique ability to deny replications, featuring the best spoofing technology available. This feature can be toggled on and off as appropriate, so for high level secure areas and to ensure no spoofs can gain access through your system, you must switch this on.

What is Liveness Detection?
Liveness detection is a form of intel that is conditioned within a biometric reader with the aim of determining whether the piece of data presented has come from an authorised, living person. There are varying forms of liveness detection technique used within a biometric system, and the type is often dependent on the biometric modality; fingerprint, face, iris, voice, etc. as some modalities are more simple to replicate than others.
Liveness detection is achieved through unique algorithms that quickly analyse the data presented to a reader to determine whether it is ‘live’, non-live (i.e. no blood flow), or a replication of the data, known as a ‘spoof’.
There are two main forms of liveness detection:
Active: This is where the reader will require a specific criteria of data from the authorised individual that cannot be replicated. For example, with a fingerprint system, the reader will use a combination of thermal imaging to detect heat and blood flow, while also analysing the unique fingerprint itself.
Passive: This form uses specialised algorithms to determine a non-live image or replica object based on the original piece of data captured during the registration process. The better the quality of the data record, the higher the matching performance will be.
These methods can be used separately, but work much better when combined to ensure that the reader cannot be tricked by any kind of spoof, no matter how sophisticated it may be. Our ievo readers harness both active and passive liveness detection technologies to ensure accuracy and a high-level of security.
What is Biometric Spoofing?
Biometric spoofing is where an artificial replication of a piece of authorised data is presented to a biometric reader in order to overthrow the authentication system and gain access to premises or assets that otherwise would not be accessible.
A fraudster would use a replication, known as a spoof, in order to attempt to impersonate an authorised individual. This can be done in a number of ways and again the form of spoof depends on the biometric modality.
A fingerprint spoof can be created using a variety of materials, including gelatine, silicone, latex and even wood glue. This is usually done by taking an original stored fingerprint and applying it to a ‘fake finger’.
Why is Liveness Detection Important?
Liveness detection is incredibly important in biometric access control systems, as in order to have complete assurance that authorised individuals only will be granted access to whatever or wherever you require restricted access, you need to be sure that only that person’s individual genetics are recognised by your biometric reader system and that this can never be reproduced or spoofed.
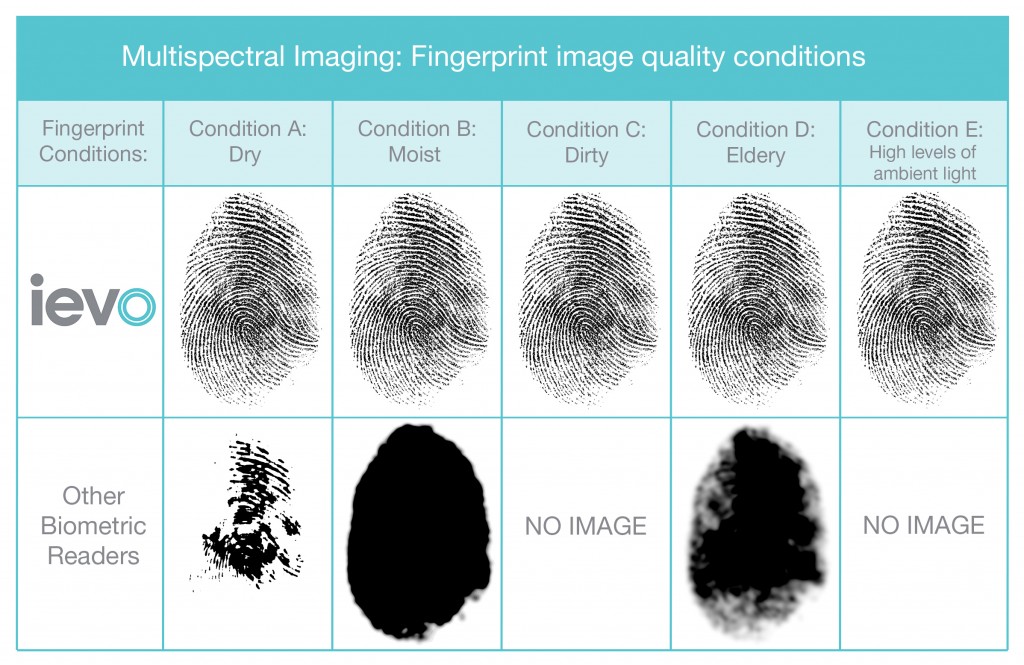
The ievo Ultimate system has the ability to function with liveness detection to prevent even a highly accurate replica from defeating the access control. This is because our readers use multispectral imaging technology that can detect flesh from non-living flesh by reading the fingerprint surface and subsurface levels up to 4mm deep.
This level of security is further enhanced by the way our systems record fingerprint data. Each fingerprint is recorded and converted into a mathematical algorithm that is a mere representation of the print itself, known as a biometric template, and then this template is stored on our control boards. The original print is never stored, which means that no sensitive data is kept in a form that can be replicated and therefore would not be of any use to a criminal if stolen.
How do ievo readers work?
Now you have a better understanding of the enhanced level of security that installing an ievo system within your business can offer, you may be wondering what else our readers can do.
ievo readers integrate with an extensive range of sophisticated access control systems and platforms to enable you to customise access levels across your entire premises. This works by the reader itself communicating with your chosen access control system and limiting access according to the rules that have been setup within this system.
This means that you can give various employees varying levels of access to different areas and assets within your business. You can even control this by specific times, meaning that employees may only be granted access during the hours of your choice.
Not only does this allow you to control access levels, but should any suspicious events occur within the premises, you will be able to instantly see who has access to which area at which time to determine the cause.
You can customise the level of access in the following ways:
(Please note, the level of customisation depends on which access control system you integrate with the ievo reader.)
By job role
By department
By working hours / days / weeks / months (or limited hours)
By employee ‘type’ - e.g. zero-hours contract workers
By seniority / status / responsibilities.
You can also select a combination of these to heighten security within your business, and these limitations can even be customised by each individual reader that you have installed. This system can also be used as a time and attendance management tool too, to better inform your payroll.
This vast level of customisation ensures only the right people gain access to areas based on a whole host of criteria, meaning that your areas have never been safer. To heighten this security, choosing the right access control system to work alongside your ievo readers is a must.
A sophisticated system will allow your chosen access criteria to be adjusted instantly, so if you need to alter the levels of access for specific employees as the progress or leave the business then you can quickly and simply do this.

To find out more about how ievo systems can improve your business specifically, get in touch with a member of our team today.
Case Studies
Want to know more? Simply read one of our many case studies to find out how ievo readers have improved the security of our customers.

